I have a bunch of test CentOS/FreeBSD servers and I wanted to get all the notifications sent to my e-mail instead of logging to each server and check the status of each one of them. Some of my servers are behind my home network where outbound port 25 (SMTP) is blocked by the ISP. So, I decided to use my main postfix server which is already configured to use port 587 for SMTP using TLS. In this post, I’ll explain how I configured my test servers to relay e-mails.
Use the following links to see how I configured the postfix main server for CentOS and FreeBSD.
Table of Contents
CentOS 7
There are some prerequisites for CentOS 7. It comes with postfix installed and it has built-in Cyrus SASL already, but we need another Cyrus SASL package for login support. In addition, CentOS doesn’t come up with the mail command, so we have to install that as well.
Prerequisites
Install Cyrus SASL package and the mail client.
yum install cyrus-sasl-plain mailx
postfix main config file
Edit /etc/postfix/main.cf and add these lines at the end.
relayhost = [server.domain.com]:587 smtp_sasl_auth_enable = yes smtp_sasl_security_options = noanonymous smtp_sasl_password_maps = hash:/etc/postfix/sasl_passwd smtp_use_tls = yes smtp_tls_CAfile = /etc/ssl/certs/server.domain.com.crt
The first line is your main postfix server that will receive the e-mail from the client servers, the 4th line is the file where you are going to store the username and password for the user that’s able to login to the main postfix server and the 6th line is the certificate of the main postfix server.
SASL Authentication
Edit /etc/postfix/sasl_passwd and add this line.
[server.domain.com]:587 [email protected]:YourPassword
You have to specify your main postfix server, the username and the password for a valid user that’s able to login to that server and receive e-mails. Once completed, execute postmap.
postmap /etc/postfix/sasl_passwd
e-mails to relay
I wanted to send all of my root e-mails to my main server, so what you have to do is edit /etc/aliases and scroll all the way down at the bottom. Un-comment the root line and specify where do you want your root emails to be forwarded.
root: [email protected]
If you have some cron jobs that run under some other username, specify them in this file, e.g. someuser: [email protected].
After you are done, type newaliases.
newaliases
Public certificate
You will also need the public certificate of your e-mail server. Get the certificate in a PEM format and paste it into a new file /etc/ssl/certs/server.domain.com.crt. Or, in my case, I have a wildcard certificate for my domain, so I can get it using this command.
openssl s_client -connect server.domain.com:443 < /dev/null | \ sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > /etc/ssl/certs/server.domain.com.crt
Final step
Restart the postfix server on the client server, send a test e-mail and check the result.
systemctl restart postfix echo "This is a test." | mail -s "Test e-mail" root tail /var/log/maillog
FreeBSD 11
Unlike CentOS, FreeBSD doesn’t come up with postfix, instead it uses sendmail. So, we have to remove sendmail, install postfix and follow similar config as with CentOS.
Prerequisites
We have to install postfix from the ports because it doesn’t come up with Cyrus SASL. It comes with dovecot SASL, but I am not sure if it works in a client config. On the other hand, FreeBSD comes with mail installed. Install the postfix port, not the package.
cd /usr/ports
If you get an error that there is no such file or directory, get the ports tree. If you can cd to that folder, skip the step below to install the ports tree.
portsnap fetch portsnap extract
Install postfix.
cd /usr/ports/mail/postfix make all install clear
When this dialog box pops-up, select BDB and SASL as highlighted.
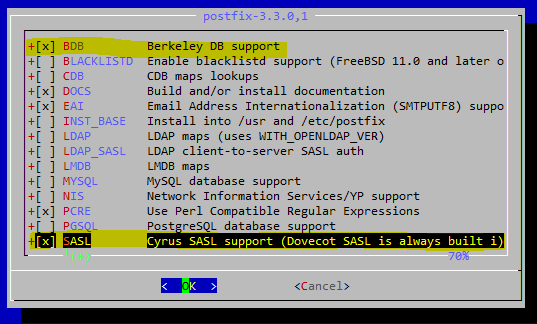
Execute these lines so you replace sendmail with postfix.
sysrc postfix_enable="YES" sysrc sendmail_enable="NONE" mv /usr/local/etc/mail/mailer.conf /usr/local/etc/mail/mailer.conf.old install -m 0644 /usr/local/share/postfix/mailer.conf.postfix /usr/local/etc/mail/mailer.conf
Add the following lines to /etc/defaults/periodic.conf
daily_clean_hoststat_enable="NO" daily_status_mail_rejects_enable="NO" daily_status_include_submit_mailq="NO" daily_submit_queuerun="NO"
Make sure Cyrus SASL is installed.
postconf -a
You should see cyrus and dovecot there.
postfix main config file
Edit /usr/local/etc/postfix/main.cf and add these lines at the end.
relayhost = [server.domain.com]:587 smtp_sasl_auth_enable = yes smtp_sasl_security_options = noanonymous smtp_sasl_password_maps = hash:/usr/local/etc/postfix/sasl_passwd smtp_use_tls = yes smtp_tls_CAfile = /usr/local/etc/ssl/server.domain.com.crt
The first line is your main postfix server that will receive the e-mail from the client servers, the 4th line is the file where you are going to store the username and password for the user that’s able to login to the main postfix server and the 6th line is the certificate of the main postfix server.
SASL Authentication
Edit /usr/local/etc/postfix/sasl_passwd and add this line.
[server.domain.com]:587 [email protected]:YourPassword
You have to specify your main postfix server, the username and the password for a valid user that’s able to login to that server and receive e-mails. Once completed, execute postmap.
postmap /usr/local/etc/postfix/sasl_passwd
e-mails to relay
I wanted to send all of my root e-mails to my main server, so what you have to do is edit /etc/aliases and scroll a little bit way down. Un-comment the root line and specify where do you want your root emails to be forwarded.
root: [email protected]
If you have some cron jobs that run under some other username, specify them in this file, e.g. someuser: [email protected].
After you are done, type newaliases.
newaliases
Public certificate
You will also need the public certificate of your e-mail server. Get the certificate in a PEM format and paste it into a new file /usr/local/etc/ssl/server.domain.com.crt. Or, in my case, I have a wildcard certificate for my domain, so I can get it using this command.
openssl s_client -connect server.domain.com:443 < /dev/null | \ sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > /usr/local/etc/ssl/server.domain.com.crt
Final step
Restart the postfix server on the client server, send a test e-mail and check the result.
service postfix restart echo "This is a test." | mail -s "Test e-mail" root tail /var/log/maillog
You will notice that the e-mails that come from FreeBSD are always sent by Charlie Root. If you have multiple FreeBSD boxes, the e-mails from various FreeBSD servers will come as Charlie Root which might be a bit confusing. So do a chpass and change the line Full Name, so instead of Full Name: Charlie &, do something like Full Name: servername Charlie &.
chpass

Do

