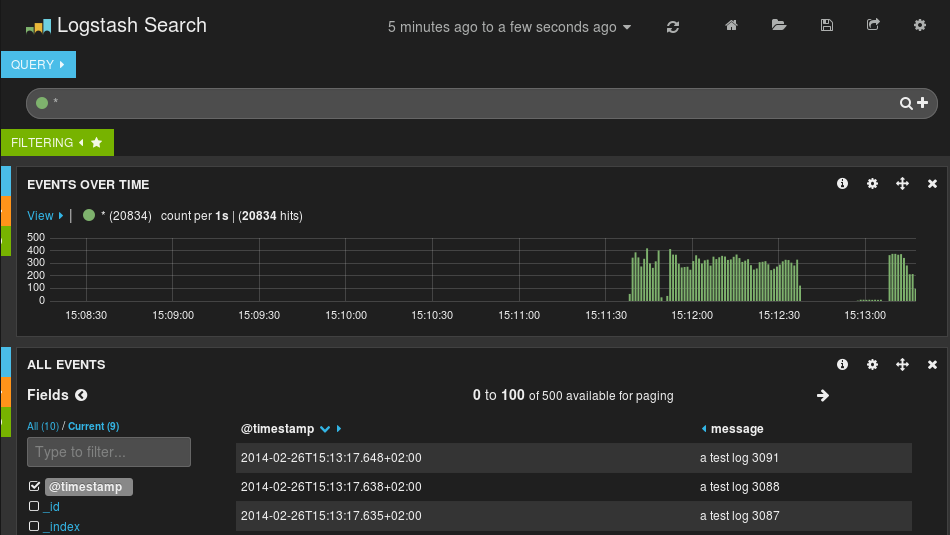
In this post, I’ll explain how to configure a rsyslog server and client on various operating systems. For the servers, I’ll chose 2 Red Hat 7 servers and the clients will be AWS Linux, FreeBSD and Windows 2016.
rsyslog is an open-source utility for logging, a derivate of the original syslog. As defined by RFC 3164, each message includes the facility code and severity level.

The severity levels are these. (Both screenshots are from Wikipedia).
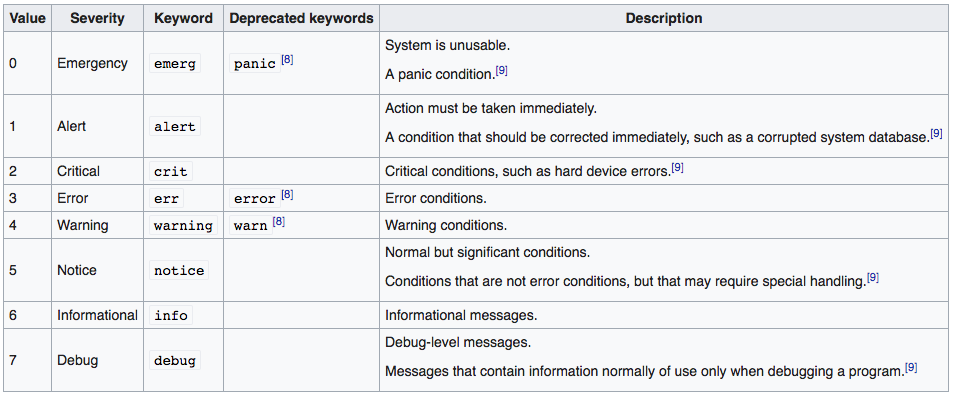
Table of Contents
RHEL 7 rsyslog servers
RHEL 7 comes with rsyslog installed by default. Make sure it’s running.
systemctl status rsyslog
The configuration file is /etc/rsyslog.conf. Make sure that these lines are uncommented. They tell the rsyslog daemon to accept TCP and UDP connections.
# Provides UDP syslog reception $ModLoad imudp $UDPServerRun 514 # Provides TCP syslog reception $ModLoad imtcp $InputTCPServerRun 514
If you make changes in /etc/rsyslog.conf, make sure you verify the config.
rsyslogd -N 1
If you make a change, you’ll have to restart the rsyslog daemon.
systemctl restart rsyslog
To test if rsyslog works fine, try a test.
logger -p local0.notice -t from_cmd_line "Test Message"
If you check the /var/log/messages, a file where by default rsyslog writes the output, you’ll see the message.
tail /var/log/messages
![]()
OK, so we didn’t have to make any changes on both RHEL servers. Let’s move to the clients.
NOTE: If you have firewalld enabled, you’ll have to open the ports for the clients.
firewall-cmd --permanent --zone=public --add-port=514/tcp firewall-cmd --permanent --zone=public --add-port=514/udp firewall-cmd --reload
AWS Linux, RHEL 6, CentOS 6
AWS Linux is based on RHEL 6 so the instructions will apply for all of them. Check if rsyslog is running.
service rsyslog status
Edit /etc/rsyslog.conf and make sure these lines are commented. We don’t want a server, we want a client.
# Provides UDP syslog reception #$ModLoad imudp #$UDPServerRun 514 # Provides TCP syslog reception #$ModLoad imtcp #$InputTCPServerRun 514
Add these lines (11 to 14) somewhere at the end.
#$WorkDirectory /var/lib/rsyslog # where to place spool files #$ActionQueueFileName fwdRule1 # unique name prefix for spool files #$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible) #$ActionQueueSaveOnShutdown on # save messages to disk on shutdown #$ActionQueueType LinkedList # run asynchronously #$ActionResumeRetryCount -1 # infinite retries if host is down # remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional #*.* @@remote-host:514 # ### end of the forwarding rule ### *.* @@10.0.0.170 $ActionExecOnlyWhenPreviousIsSuspended on & @@10.0.0.225 $ActionExecOnlyWhenPreviousIsSuspended off # Finally include all config files in /etc/rsyslog.d. This allows overrides # of the default configuration above. $IncludeConfig /etc/rsyslog.d/*.conf
These four lines means that my primary rsyslog server has an IP of 10.0.0.170 and in case it’s not reachable, use the server 10.0.0.225. Line 11 tells the rsyslog client to log everything to the server. If you want only certain messages logged, than you can change it, e.g. instead of *.* @@10.0.0.170 you can use something like *.info @@10.0.0.170 or *.info;auth.err @@10.0.0.170. Look at those two tables above. If you run this command on the client.
logger -p local0.notice -t from_aws_linux "Test Message"
and do
tail -f /var/log/messages
on the server, you’ll see the message on the server, not on the client.
FreeBSD
FreeBSD uses the old syslog, not rsyslog, but we can still redirect the logs to our RHEL servers. Edit /etc/syslog.conf and all the way at the end add this line.
*.* @10.0.0.170
As you can see, syslog uses one @, not two @@s. Restart the service and send a test message. You’ll see that the message goes to the RHEL server now.
service syslogd restart logger -p local0.notice -t from_FreeBSD "Test Message"
Windows
Go to this link and download the rsyslog client. You can see the link for the download and also for the manual.
The rsyslog agent for Windows is very detailed and requires some studying. Use the manual, there are some examples there. I’ll show you how to forward the event ID 7036. This event gets triggered when a service changes its state. So, download the client and open up the GUI. Expand the following and click on Rsyslog. Enter the primary and secondary rsyslog server’s IPs. Click Save in the upper left corner and then click Restart.
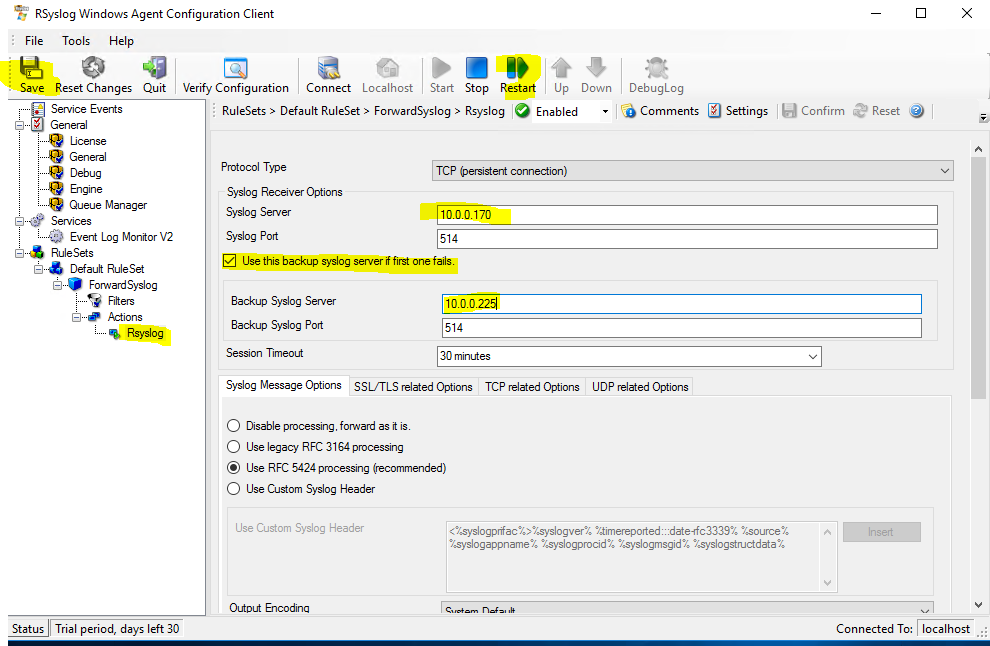
If you check the logs on your rsyslog server, you’ll see a lot of logging going on. Pretty much everything that Windows does. We just want to filter all these logs to a single event ID.
So, in the Default Rule Set, click Filters, then right-click AND, choose Add Filter, Event Log Monitor and then Event ID.
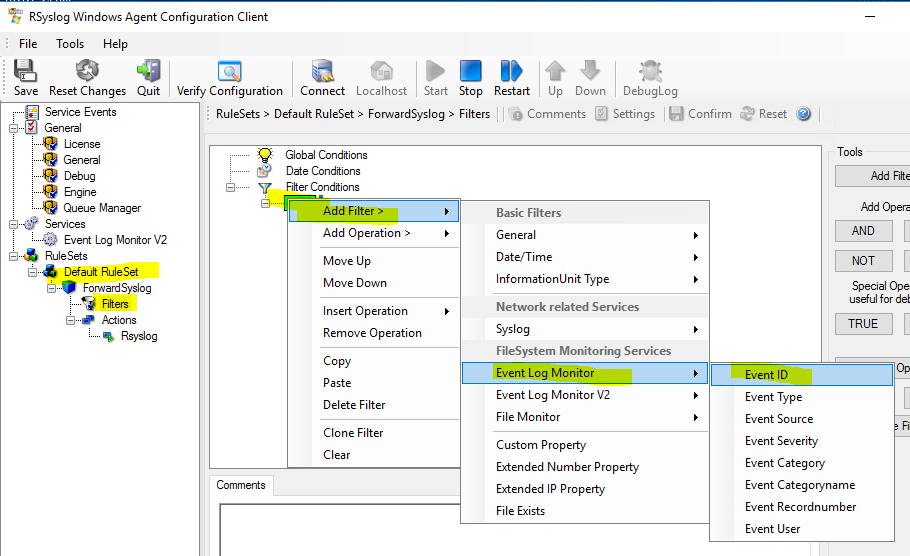
Enter the Event ID 7036, click Save and Restart.
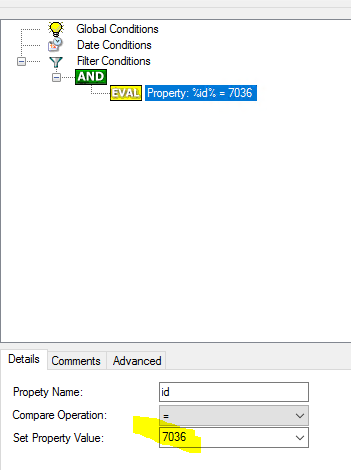
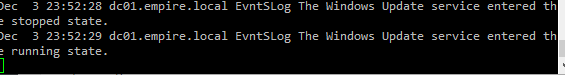
Now, go to Services (services.msc) and restart Windows Update service. You should see this on the rsyslog server.